Outrageous Info About How To Detect A Dos Attack
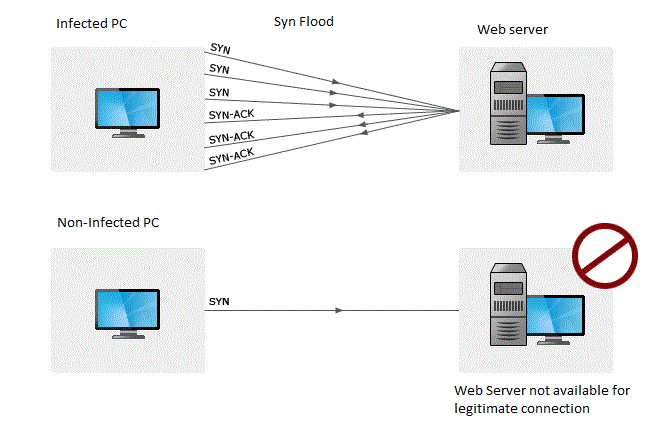
An ip address makes x requests over y seconds your server responds with a 503 due to service.
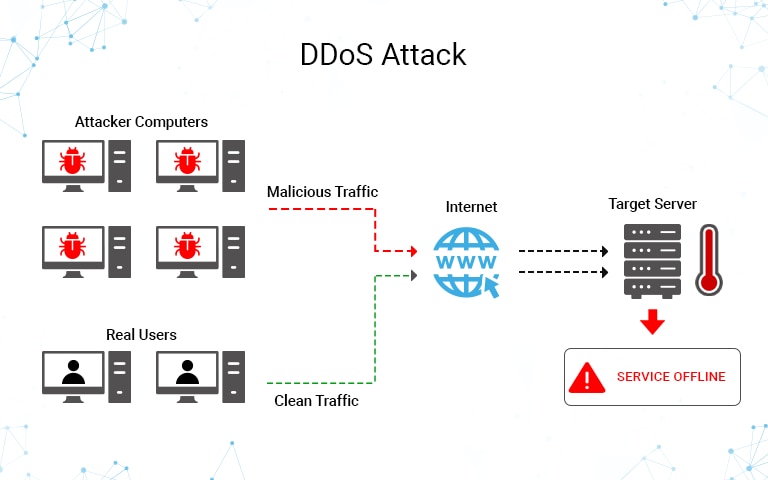
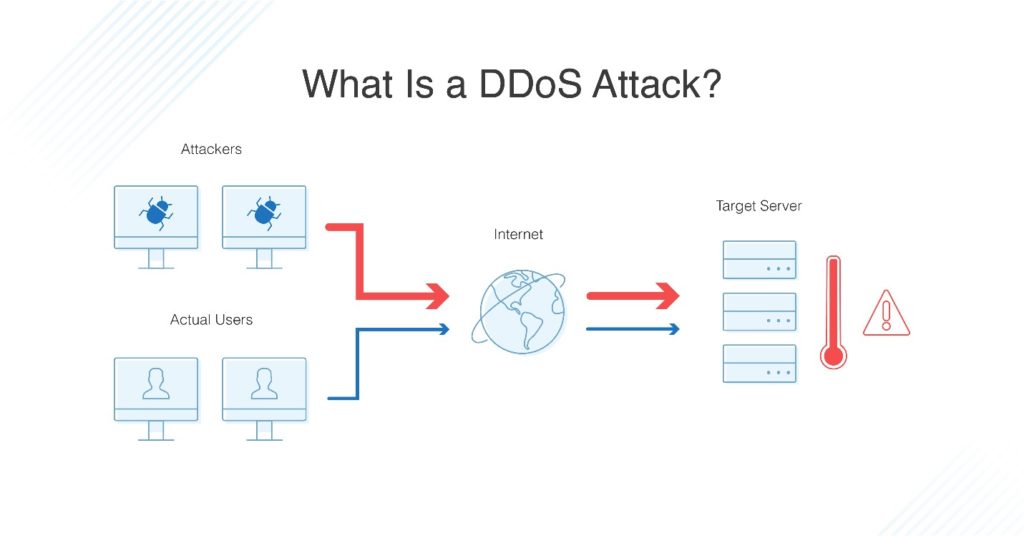
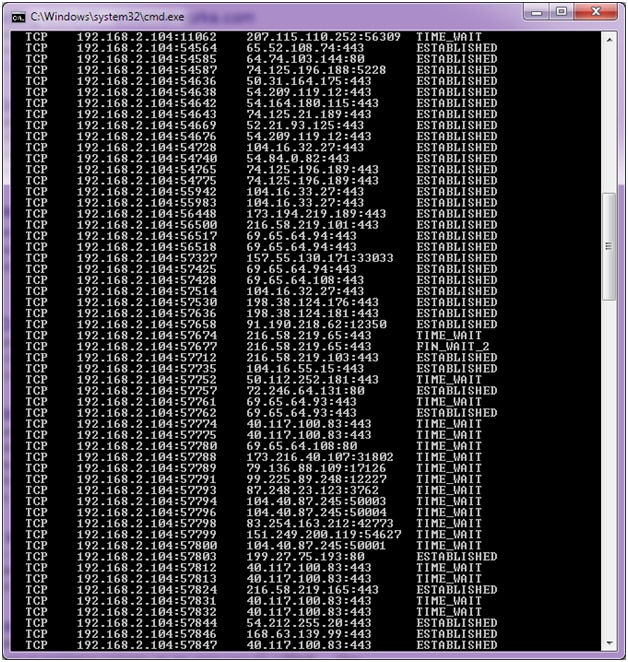
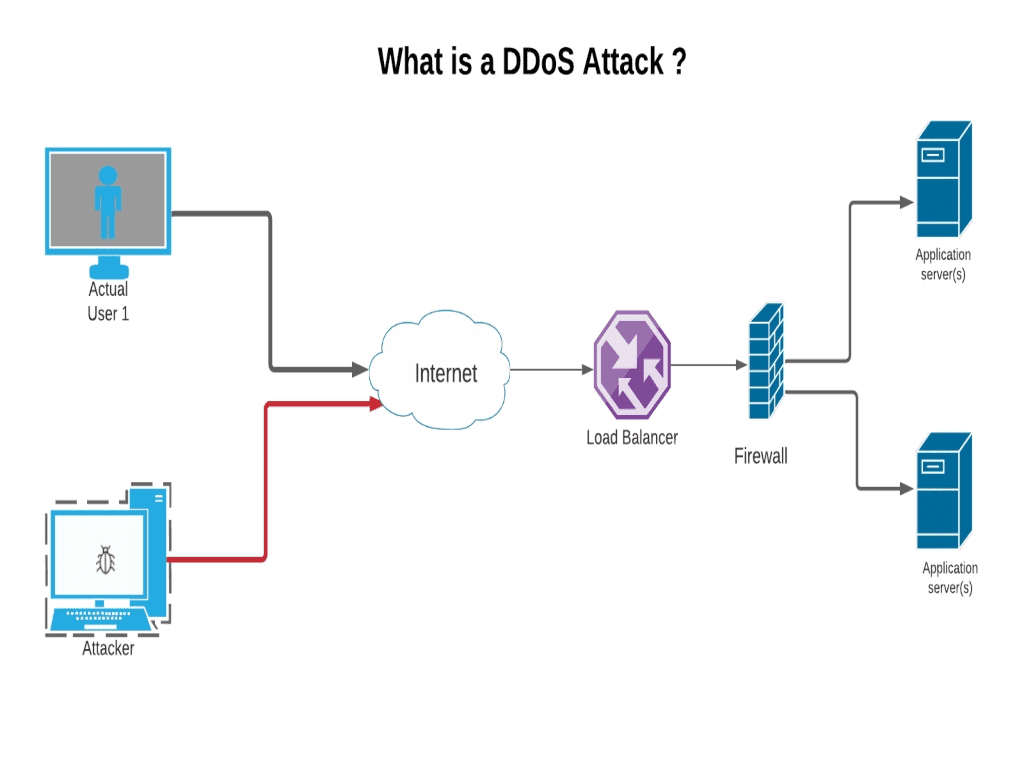
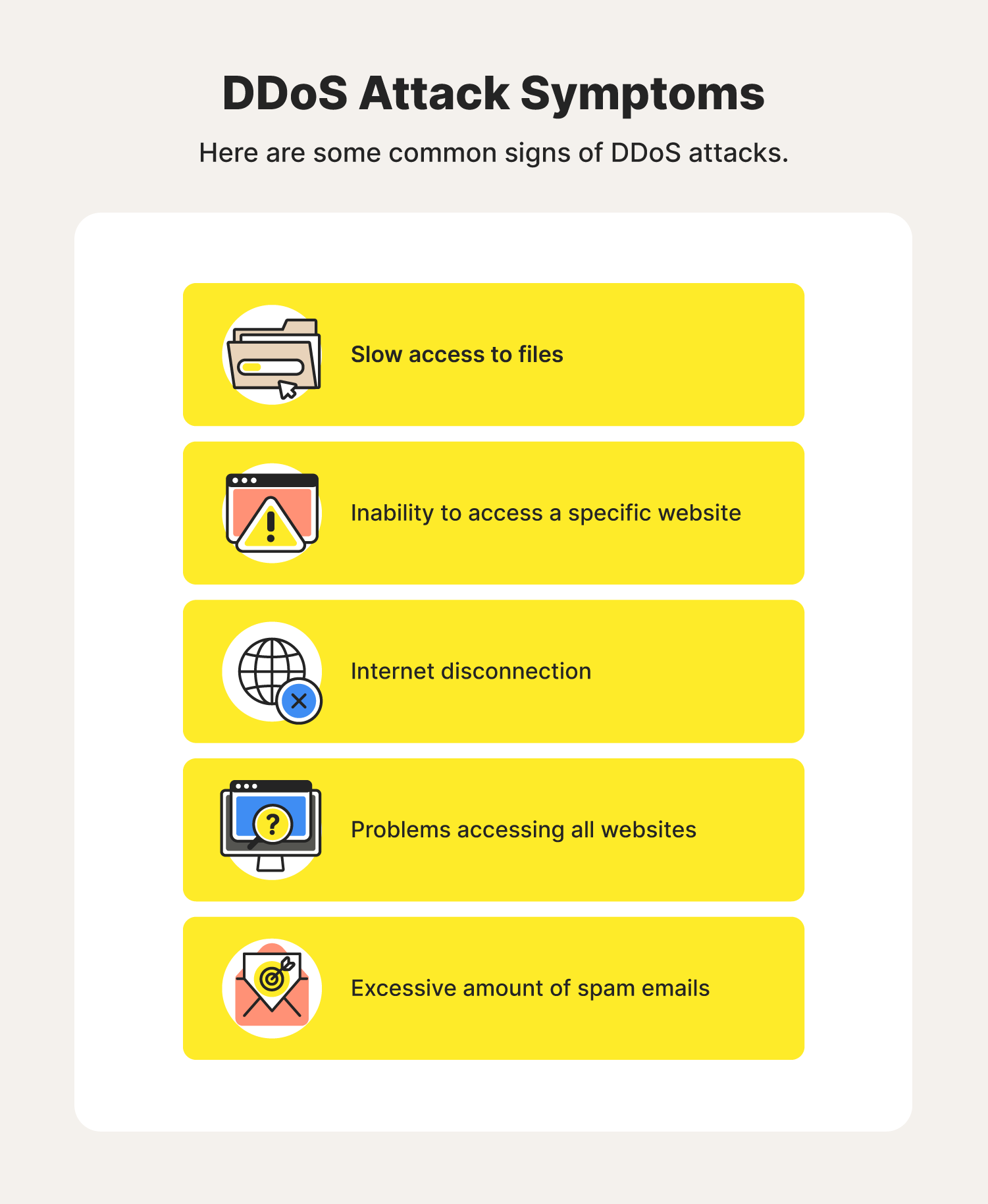
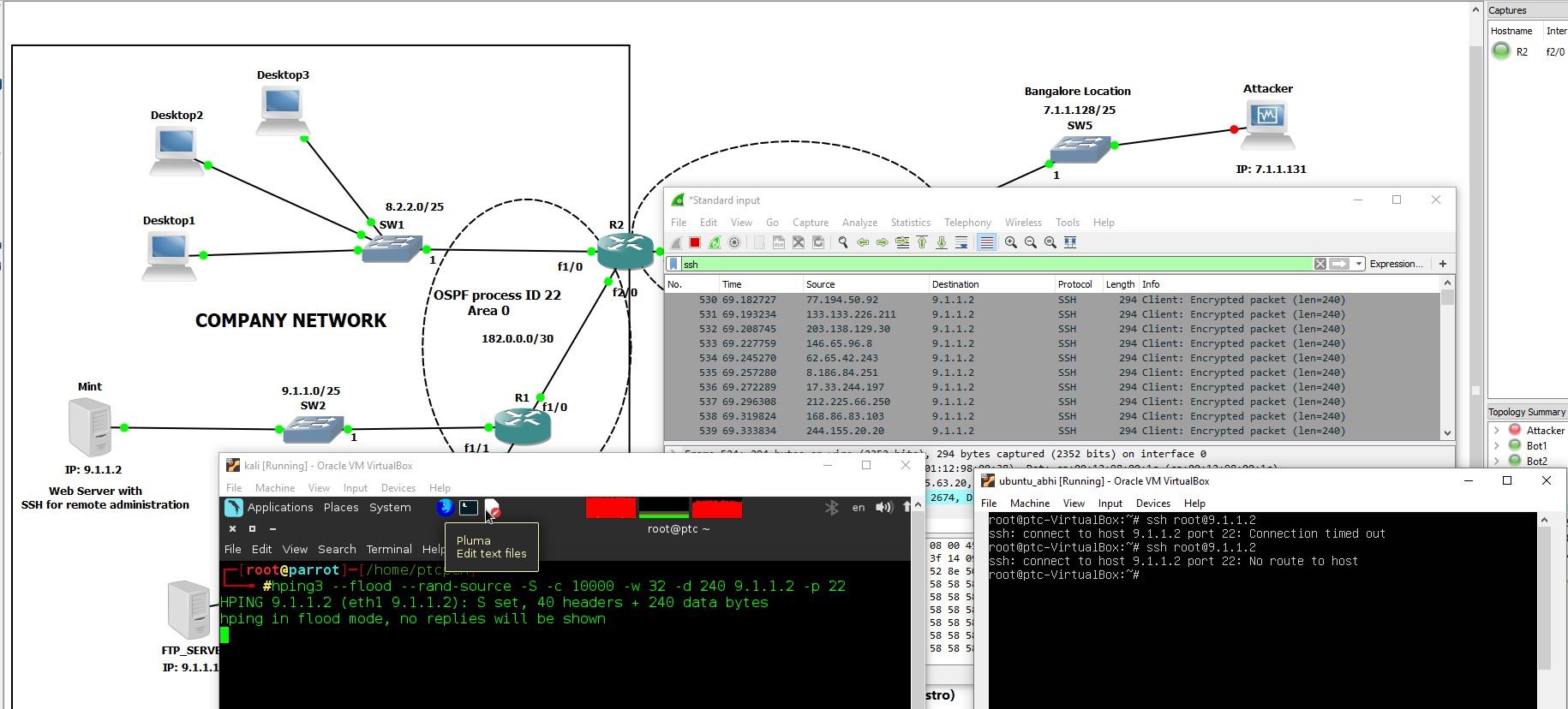
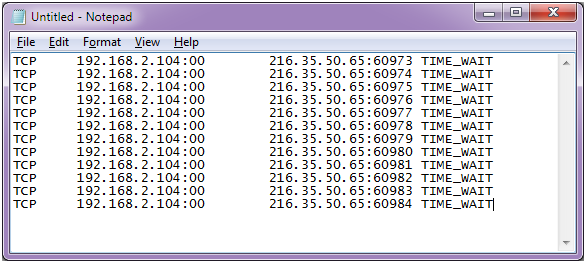
How to detect a dos attack. Even before you go and pull the server logs (more on that later) during a ddos attack, you’ll likely experience one or more of the following. Certain ip addresses send too many connection requests over a short time. You can also check your network stats and.
However, another sign of a ddos attack is a very strong spike in bandwidth. Monitoring dns activity is essential to identifying early signs of a dns flood ddos attack. You see a surge in web traffic, seemingly out of nowhere, that’s coming from the.
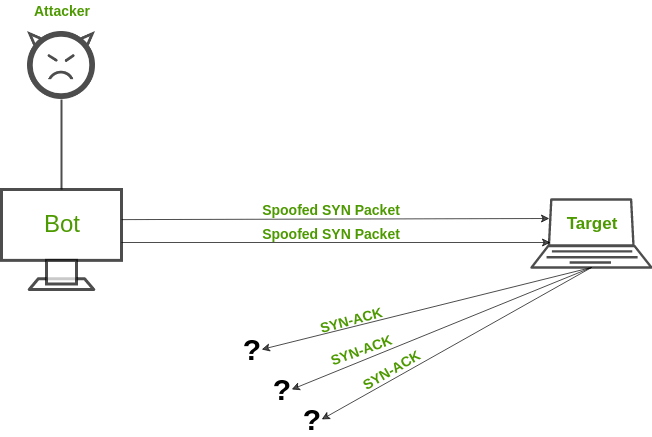
Typically, these connections don’t get completed since. You can view this by logging into your account with your web host and opening cpanel. While there’s no one way to detect a ddos attack, there are a few signs your network is under assault:
Dns uses two types of packets: Fill in the columns to send notification emails. 5 red flags when detecting ddos attacks.
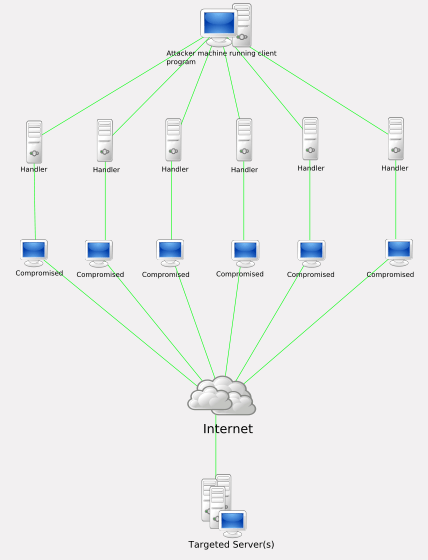
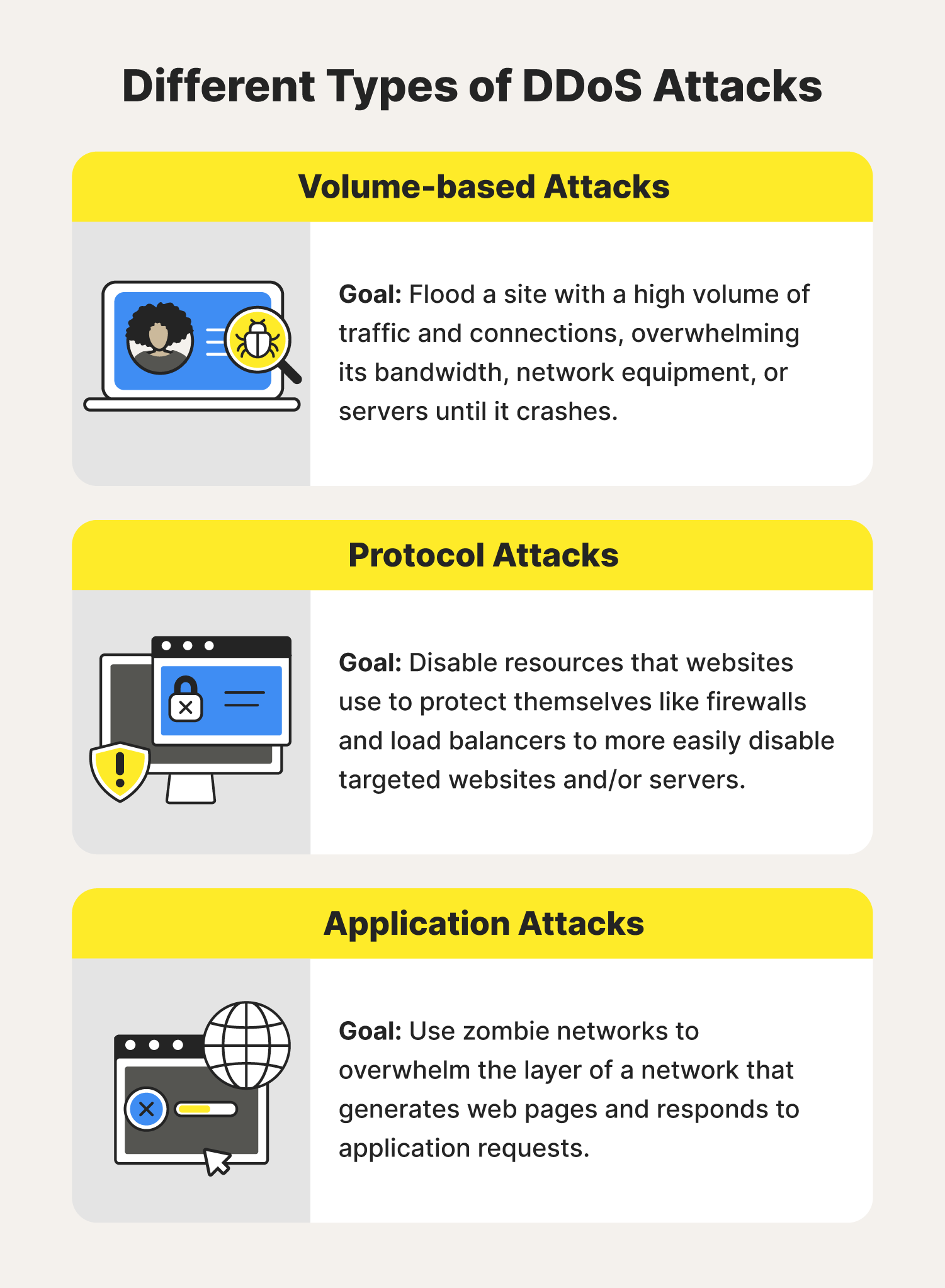
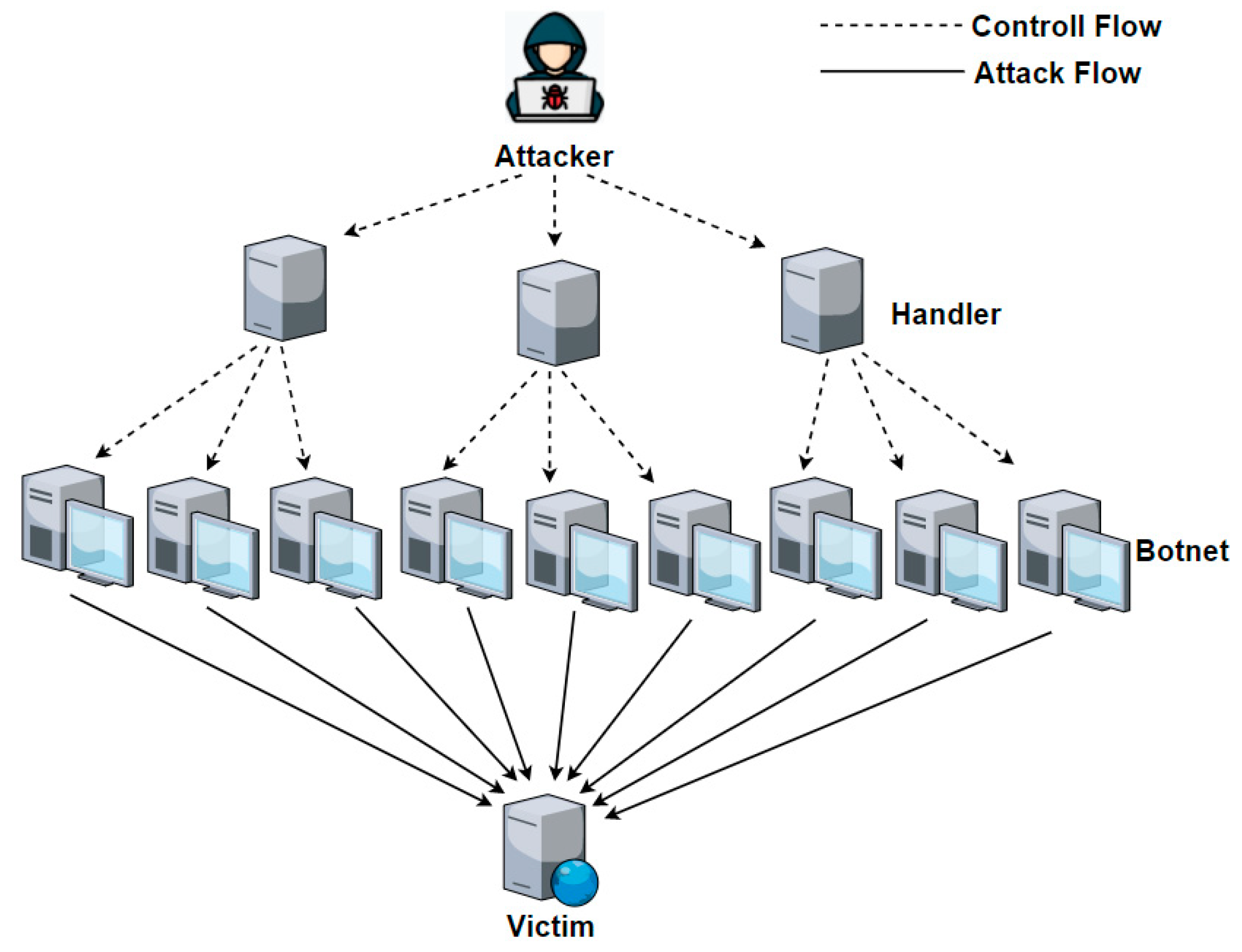
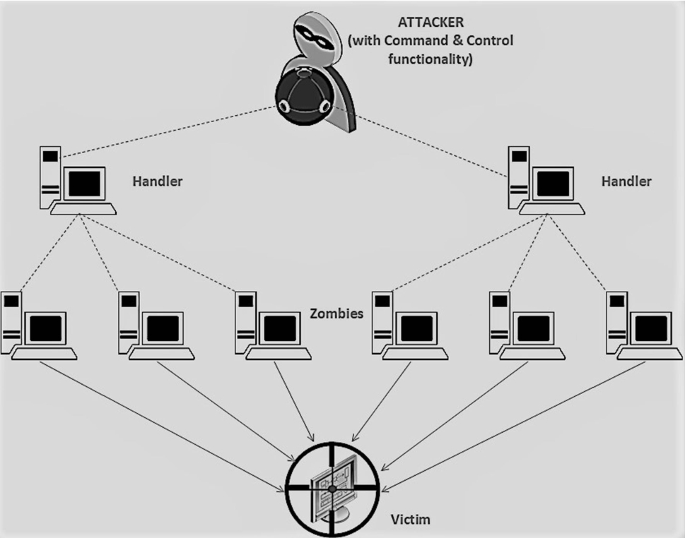
How to detect a ddos attack. It can take hours to detect and mitigate a ddos attack at significant cost to the organization. Who would i be in a horror movie buzzfeed x x
Detecting an active dos attack when a server is attacked by ddos, it slowly starts killing it’s performance. Early threat detection is the most efficient way to prevent a ddos attack. The more you know about what normal inbound traffic looks like, the quicker you'll spot the start of a ddos attack.